The Era of Predictable Cyber Attacks: Building True Cyber Resilience
By Edward Pham, December 1, 2025
Reference: 2025 Voice of the CIS
Cyber-attacks are no longer hypothetical, they are predictable. The rise of AI has accelerated both the volume and sophistication of threats, enabling attackers to generate credible phishing content, malware variations, and exploitation chains with simple prompts.
At the same time, modern organizations depend on complex, interconnected hybrid environments. This has created the largest, most volatile attack surface in history - one that changes daily.
Together, these forces have reshaped cybersecurity. Prevention alone is no longer enough. Organizations must now build the capability to withstand attacks, maintain continuity, recover rapidly, protect data, and preserve trust. This is the new era of Cyber Resilience.
The statistics reinforce this reality:
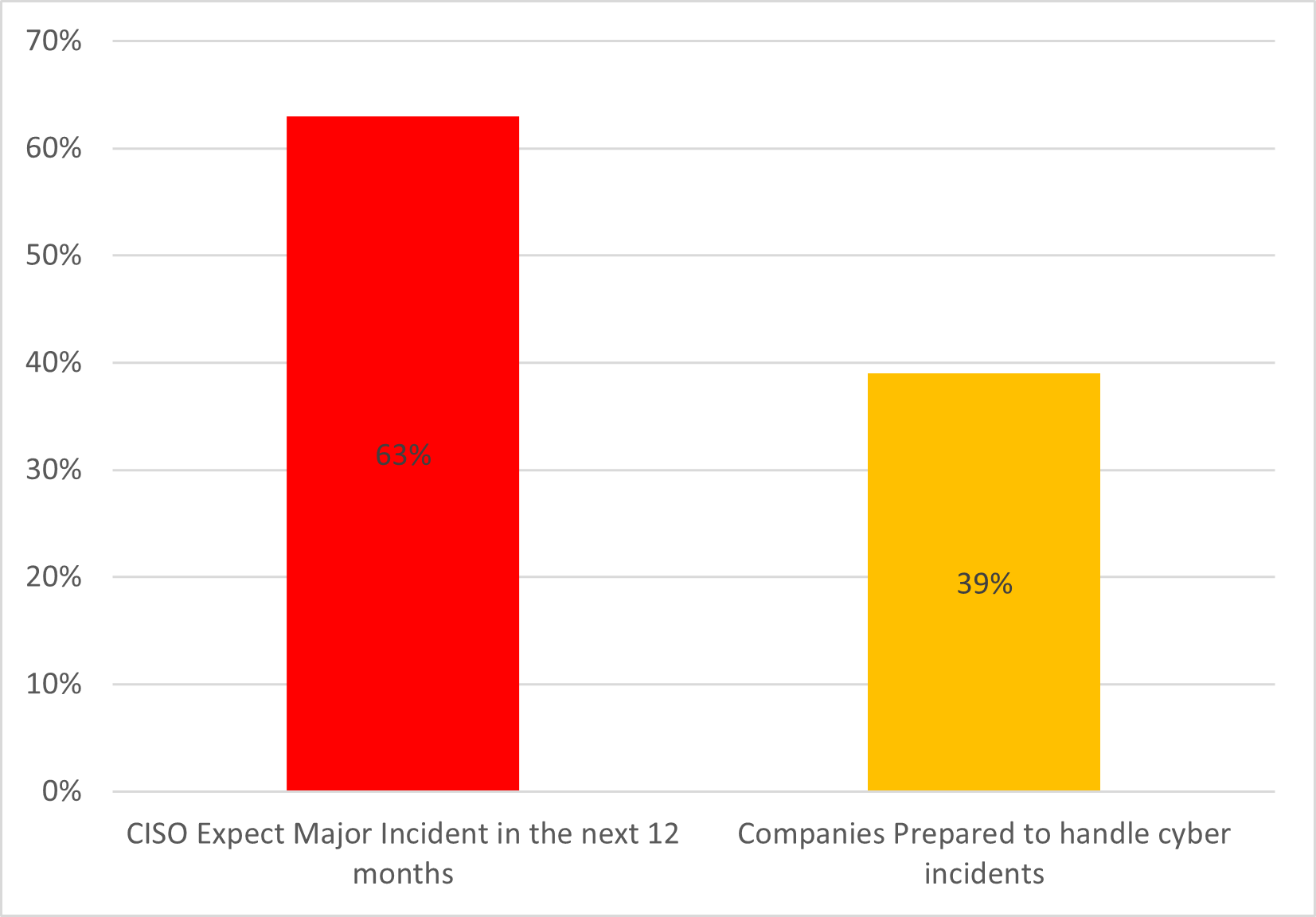
- ~63% of CISOs expect a major cyber incident within the next 12 months.
- ~61% admit their organization is not fully prepared for a targeted attack.
- Global downtime costs now reach US$9,000–23,000 per minute for large enterprises.
- Median ransom demands in 2025 are ~US$1.3M, and the average recovery cost (excluding ransom) is ~US$1.5M.
- Nearly three-quarters of large organizations report a cyber breach within the last year.
A Practical Roadmap for ITIL-Enabled Organizations
If this feels complex, you are not alone. The good news is that organizations with established ITIL processes already have a strong foundation. When aligned with the NIST framework, ITIL practices can be adapted to dramatically strengthen an organization’s security posture.
Below is a practical, seven-step roadmap that you can adapt.
1. Improve Knowledge & Training
Human error remains the #1 breach vector. Yet most training programs are outdated and ineffective. Invest in continuous education that covers modern digital risks. A strong example is the DVMS Digital Business Risk Awareness Training.
2. Strengthen Service Asset & Configuration Management
You cannot protect what you cannot see. Increase visibility across hardware, virtual resources, applications, cloud workloads, and external dependencies. Automated discovery is essential.
3. Mature Access Management
Identity is the new perimeter. Implement Zero Trust, enforce least privilege, and unify identity governance across on-prem, cloud, and SaaS environments.
4. Evolve Incident Management
Expand traditional incident processes to include a cyber-specific playbook. Define roles, responsibilities, escalation paths, and assume that during an attack critical systems may be partially or fully unavailable.
5. Modernize Change & Release Management
Cybersecurity must be embedded in every deployment. Require vulnerability scans, configuration compliance checks, and regular penetration testing before changes are approved.
6. Strengthen Availability & Recovery
Ransomware proves that backup alone is not enough. Test full-system recovery -applications, databases, configurations, and integrations - not just files.
7. Expand Business Continuity Planning
Traditional disaster recovery must evolve. Integrate cyber-specific scenarios, ensure resilience of critical applications, and perform realistic, end-to-end exercises.
Conclusion
Cyber resilience is no longer optional—it is a strategic capability. With the right roadmap, organizations can transform from cyber-vulnerable to cyber-resilient far faster than they imagine.
When you are ready to explore how to begin or accelerate your journey, I would be pleased to start that conversation with you.